A Beautiful Dream
You are leading a team in your company that is setting up Identity and Access Management (basically authentication and authorization) for the digital wing of your firm. This digital wing of your firm has, say, hosts a mobile application and a web portal of your company where you are actively developing and providing your services to tens of millions of customer base which you have globally. Congratulations, what a sine-qua-non work you are doing for your firm, protecting the identities of the tens of millions of customers who are using the firm’s mobile app and web portal by doing SSO with your identity provider which you are positioning. Fast forward to your months of assiduous work behind the scenes and you have finally set up the architecture which looks like below and guess what? you are now ready to open your doors to the world where your work will make authentication and authorization using SSO very seamless for your customer base globally! This truly deserves hails and compliments for adding value to the business, CHEERS!
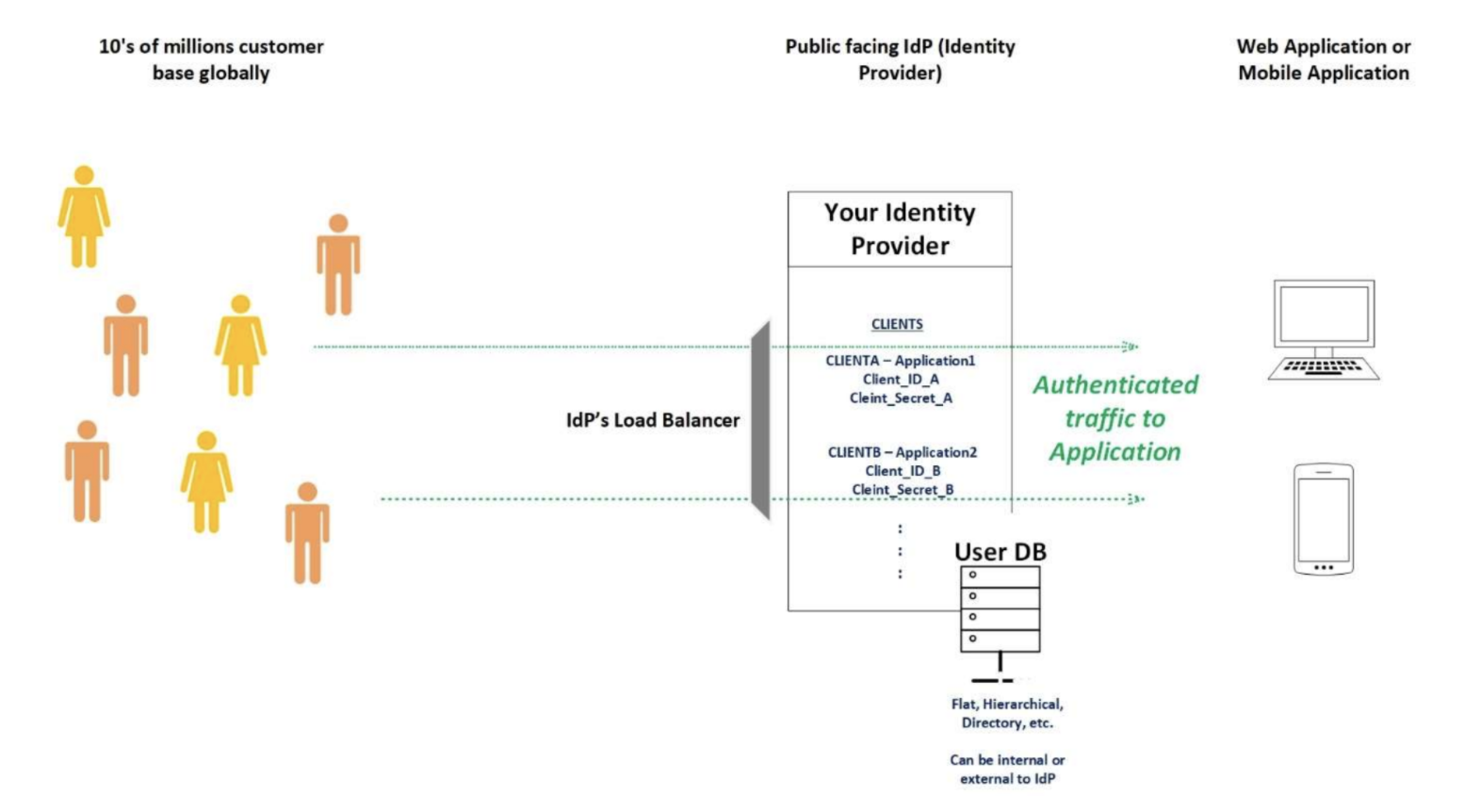
Terms Used
- IdP (Identity Provider)
- SSO (Single Sign-On)
- WAF (Web Application Firewall)
- B2C (Business-to-Customers)
- B2B (Business-to-Business)
- 2FA (Second Factor Authentication)
- IAM (Identity and Access Management)
72 hours being LIVE
- Your risk and compliance team reporting almost constant 500K-600K authentication requests per hour in the last 48 hours. Note: You have your architecture such that, you are not force logging users out for at least 3 months using Rotating Refresh Token (absolute nailed-on OIDC engineering work your team has done), therefore, you should not expect this high login traffic.
- Your actual users getting Denial of Service (DoS) as due to a very high number of requests per hour, the true users are not able to sign in.
- You have your users’ setup for SMS based 2FA and in the last 48 hours, you have been reported by your customer support team that more than 20,000 of your customers are receiving tens of 2FA SMS codes intermittently which they never requested (customer experience at its best, give customers 2FA SMS code, before even they asked for one, nailed on Engineering once again!!)
- The risk and compliance team are now your best friends, they have also reported you that they have identified an estimate of 20,000+ (and counting of course) accounts being compromised, breached, account takeovers, etc.
- Your risk and compliance team have now started to somehow quantify the losses these attacks have imposed, so far, they have reported to you that the approximate figure is looking around $2M so far and counting/increasing as these attacks continue.
What Went Wrong?
Setting up a publicly available “auth” endpoint is no joke, considering the myriad opportunities it gives the attackers all around the world is difficult to evaluate. As soon as put an “auth” endpoint public-facing with no protection/filtering mechanism on the traffic made to this endpoint it is subject to attacks which are but are not limited to Bot Attacks, Denial of Service, Account Take Overs, Credential Stuffing, etc. Therefore, it is very crucial that you have something protecting your public-facing Identity Provider and you do not really expose it to traffic directly but rather have only filtered traffic making it to your auth endpoint.
Your Magic Wand
A reverse proxied web application firewall with your Identity Provider is one of the most effective magic wands that you can make the best use of in this case, we will learn more about this, the architecture of the same, and how you can make the best use.
- What is a Reverse Proxy?
A reverse proxy is a type of proxy where the server returns resources to the client where it would appear to the network that it originated from the reverse proxy server itself. In this case, our reverse proxy is a Web Application Firewall (WAF). We are not going into technical details of how to implement a reverse proxy WAF with your IdP, but it is very simple and straightforward, and I can simply bet on you to figure out and implement it. - What is a WAF?
A Web Application Firewall is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service (in our case our Identity Provider). It empowers you to inspect each and every HTTP traffic going to your IdP (as now traffic will go through WAF) and thus take measures to respond to the attacks, identifying the attacks early enough and also preventing the attacks by actively configuring your WAF to do so.
Let’s look at the Architecture
Now that we have some background on how reverse proxy can help you save your dream from turning into a nightmare, let’s look at the architecture on how that is done?
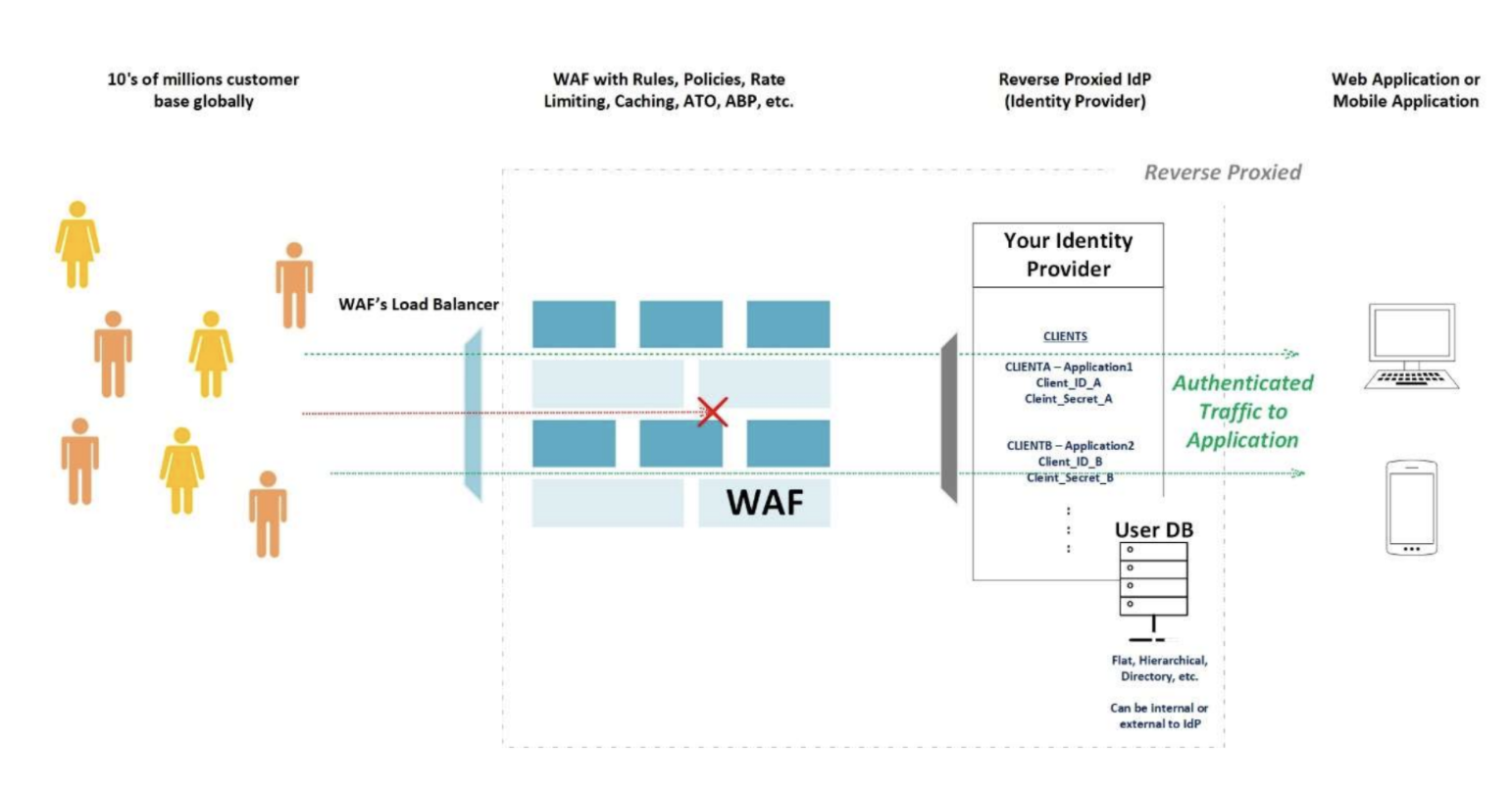
Simple isn’t it? You are basically just fronting your identity provider with a WAF which is monitoring all the traffic reaching your application. Since you can monitor the traffic you can see the traffic and actively make rules, policies, rate limiting, caching, Account Take Overs (ATO), Advanced Bot Protection (ABP), IP Throttling, Brute Force Protection, etc. Let us see some of the major benefits you get by doing the above:
1. Monitoring All the Traffic
-
- I personally like this and will always keep this feature of WAF on my number list as number one; mainly because as explained earlier WAF help you monitor all the traffic, which empowers you to see all the traffic, put it on a dashboard in real-time to monitor the type of traffic and its frequency.
- Since you also see the traffic, in case of an attack you can figure out what kind of attack it is and accordingly, you can tweak your rules, policies, rate-limiting, etc. to suppress the attack up-front.
- The only way you can be ahead of attackers is actively and most importantly identifying the attacks early enough so you can take action.
- This is again the best benefit out of WAF because say you have got it all right and everything is perfect in terms of rate-limiting, rules, policies, etc. in your WAF which is ideal to protect your IdP today, but the turnaround time for attackers to figure your protections out and then launch an attack which would bypass your current protections is usually 2 weeks. Therefore, you must continuously and actively react to the attacks that you are seeing. This is absolutely possible with WAF.
2. Rules
-
- This is another classic feature you get using a WAF, you can write rules. Rules per say to inspect the traffic and what actions to take when the rule sees a specific type of traffic.
- This really depends on what types of attacks your IdP or application sees and then accordingly you can put rules together and of course, keep tweaking them as you see attacks.
3. Rate Limiting
-
- Another definitive feature to adopt while using a WAF is to rate-limit the different types of calls coming to your IdP.
- Say for example, based on some analysis you have identified that your daily active users create about 20 user authentication requests per minute.
- To be safer and say accommodating peak user periods, you can configure a rate limit to your “auth” traffic to be 50 user authentication requests per minute.
- In this way, you are clear that if you are seeing more than 50 authentication requests per minute it is highly likely that you are under an attack.
- There are myriad options in WAF to rate-limit several other components in your infrastructure, you can rate limit auth calls, API calls, token exchange calls, etc.
- Rate limiting is best effective when it is designed well after analyzing the number of different calls that you may expect.
4. Other Features/Benefits
-
- There are of course many other benefits and features which you can get from a WAF and may be subject to licensing. For example, you can get features in a WAF like:
- Advanced Bot Protection
With growing data science and modeling WAFs can now identify bot attacks on their own based on several models that they work on, accordingly, they can take appropriate actions to stop such attacks. For example, consider a single IP address making a lot of authentication calls, the ABP can simply show them CAPTCHA, therefore, making sure it is human logging in and not a BOT. - Account Take Over
Account take over protections actively monitors the user logins and new account creation to identify valid vs invalid transactions and therefore taking certain actions if there are a high number of invalid transactions, example, multiple new account creation from one IP address. o There are other such features which are now available in modern-day WAFs especially possible due to data and models and therefore you can be sure that you will be protected against such common attacks.
- Advanced Bot Protection
- There are of course many other benefits and features which you can get from a WAF and may be subject to licensing. For example, you can get features in a WAF like:
Having a WAF in front of your publicly available Identity Provider is a very crucial piece to have in your B2C and B2B domain projects specifically. It is a good investment and a route to go into which will really save you from going through a farce but rather saving your rosy dream of providing your customers globally a SSO experience across multiple digital services which your firm is building for getting customers closer to your services digitally. And of course, cannot end this without the inevitable, for any of your questions, we are here, and we do provide expertise in such or any of your IAM solutions you may or want to build; rest assured, we are your trusted advisors in Next Generation IAM. Let us know, cheers!